QPP 41: Nick Selby on Cybercrime and Cyber Security
Nick Selby, the original co-host of this very podcast, comes back to talk about cybercrime security. What it is, why it matter, and what police departments can do better.
Episode:
https://www.spreaker.com/episode/44055818
In the episode we discuss this NPR piece by Martin Kaste. And this article in USA Today, by Nick Selby.

Here’s a screen shot of the kind of information the app offers:
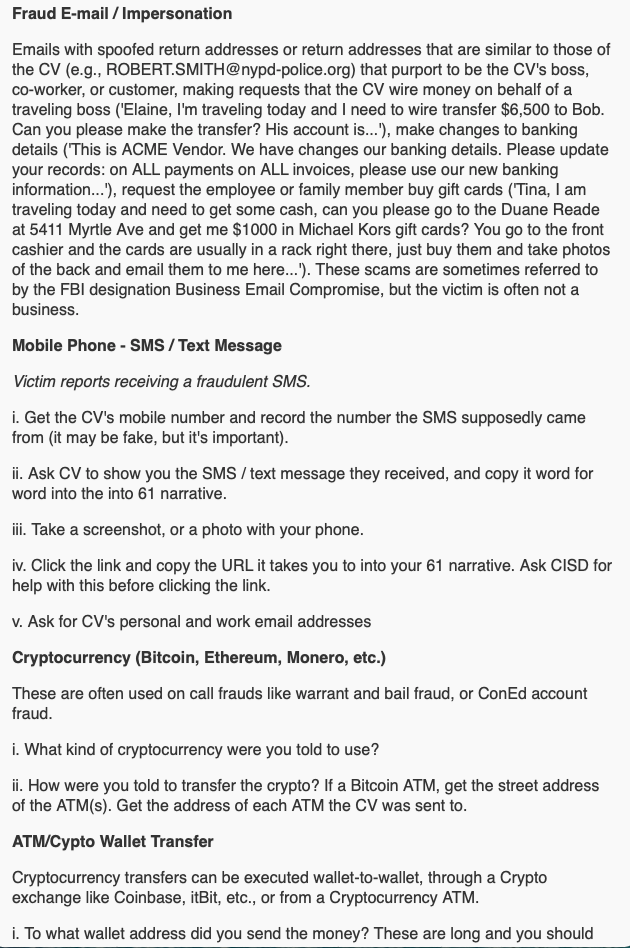
If you are law enforcement and would like to learn more about this FREE app to help your department respond to cybercrime, leave a message for Nick Selby at 917 410-0291. No, he’s not pushing some consultant fee-for-service thing. He’s just trying to help.
Here’s the youtube, for those who choose that lifestyle.
RSS feed: https://www.spreaker.com/show/2759815/episodes/feed
Uncorrected Transcript:
[00:00:04] Hello and welcome to Quality Policing. I’m Peter Moskos and ironically, whoa, it’s like a blast from the past. Long time listeners, you may recognize Nick Selby because this podcast was actually his idea.
[00:00:20] And we did the first like thirty two episodes together. Then Nick, then we had a falling out over, I think was it was a pursuit policy or something.
[00:00:31] No, I got a job and let me talk to you anymore. Yeah. Nick got a job in the NYPD and had to stop his podcast contribution, but he just gave me a call and said, I want to talk about something. Can I be on the podcast? I was like, yeah, I’m out right now, about now. So, Nick, what do you want to talk about?
[00:00:57] So when I was when I was at the NYPD, the the main project that I got involved with was trying to understand how cybercrime affected people. And it was it was kind of interesting because this is, you know, the NYPD, the agency that counts everything. And yet they weren’t counting cybercrime. They did a great job with identity theft, really. I mean, really good. And they they came up with these policies over a few years because it’s really difficult to get new stuff into the system. But they figured it out. And that’s actually a podcast in and of itself. Just how unmap can make a new policy and figure out every possible way that it can be screwed up at every stage. Oh, man. What’s up, man? Oh, man. Is the Office of Management and Planning, I think. And they’re the ones who actually figure out the process, like, how do you OK, you know, we want the cops to do something. How they got to put it in the patrol guide. They have to do training. They have to do all these things. And this is the logistics are astounding at the the scale that NYPD has to has to deal with.
[00:02:04] So we’ll say NYPD has the benefit that they have something like, oh, my. But again, my God, it’s a bureaucratic organization with thirty five thousand cops. And I don’t know how many more civilian employees. I think it’s like me. I’m off of a it’s the classic, you know, tanker that and sometimes it gets stuck in the Suez Canal. That’s exactly it’s a big organization. Look, I’ll say this by city standards and there’s a lot more efficiency and accountability than other city agencies. But that’s a low bar.
[00:02:36] I mean, but it does. It really does. And they’re and they’re very good at moving huge things at scale. And, you know, it’s a good analogy, you know, just like a tanker. I mean, it can’t turn on a dime. But once it starts that turn, look out because, you know, they’re turning and they’re going and there’s no there’s no way back.
[00:02:52] So a friend of mine who probably would like to be named, but I won’t name them, described the NYPD as what’s the big dinosaur in Jurassic Park.
[00:03:01] And he said, I probably and he said it takes a while for the NYPD to notice you and I will turn and it might twist. And finally but he’s like, once that motherfucker starts chasing you, they’re going to get you. Yeah. Yeah.
[00:03:15] Objects in mirror are closer than they appear. It’s absolutely true. So when, you know, when I first got there, the thing that I that I saw and I was talking to Commissioner O’Neill and Commissioner Miller in the in the giant conference room and I was like, we don’t know. We know that they’re scams. We know that the people are getting calls, but we don’t know what the most popular scams are and we don’t know the demography. Like, is this just little old ladies in Queens or is this is this, you know, across the board? We have we don’t we have no way of knowing. And we also don’t know how much money is lost. We think it’s a lot because when we hear about it, you know, and I think the most incredible thing is that everybody I talked to had a relative, you know, usually a mom or dad who had been taken for usually five to fifteen thousand dollars by these call scammers. And we kind of were in this netherworld. And we are I mean, law enforcement in America is still in this netherworld where it’s like, wow, you know, it’s not really identity theft. I think I read something. I think you got to call the FBI. And when, you know, you call the FBI and they’re like, oh, yeah, go to the I see three website and fill in a form. And I was talking and O’Neal was like, you know, that’s really stupid. We should probably fix that. And and so I got former NYPD Commissioner O’Neal and he kind of had the blessing above. And Commissioner Miller was also very interested in this. To Chief Galardi in the intelligence Greller Sorry, I’m just.
[00:04:52] You’re saying everything. People aren’t going to know who they are.
[00:04:55] I don’t know what’s Mueller’s title or the Deputy Commissioner for intelligence and. Chief Clode is the chief of intelligence chief executive officer, and they were like, OK, you know, it’s harmless enough. They didn’t know what to do with me anyway. So they were like, OK, you know, take a look at it. And it took a long, a long, long time because I found out since we’re not counting it, finding out how big the problem was was an adventure, like just a deep dove into the bowels of the of the record system, which, as you know, is just gigantic. And we finally figured out ways of searching for how many people were reporting. And then over months and months and months, we got to the point where we had enough information. We figured out the size of the problem and we made an estimation that it was two hundred and fifty million dollars a year. In New York City. Yeah, and to put this into perspective, that year, this was this is the previous year like 2018, car theft was about 52 million.
[00:06:00] And, you know, 250 is more.
[00:06:05] There’s also there’s something about these crimes that is worse than the monetary loss, you know, in cars are covered by insurance, but also because these crimes are designed to take advantage of vulnerable people. Yes. And sometimes it’s people who, you know, have diminished. I mean, sometimes they’re really vulnerable. Other times, you know, my mom got a call from someone who knew his grandson’s name and she didn’t fall for it, but she, like she was going along for a bitch. Why would you know? Yeah. Yeah, they knew. And her grandson, we were mentioning that, like.
[00:06:43] Well, I didn’t ask that. They said they did. Well, they said that they knew. And here’s the thing. Like one of the most common scams, when they do when they do get an elderly person on the phone or when they figure out that it’s an elderly person, sometimes they’re just calling around and they they listen for the sound of an elderly person, which is, you know, it’s you can do it.
[00:07:00] And what they’ll do is they’ll pretend that they’ve been in an accident and they’re like grandma, grandma and then the grandkids and you.
[00:07:09] That’s exactly what happens.
[00:07:10] Yes. I can’t talk. I was in an accident. Here’s my lawyer. I’m under arrest.
[00:07:16] And now they put the scam guy on the phone and he’s like, I’m Eddie’s lawyer. And and so it feels like they know who he is. And a lot of times they don’t really know who he is. These things are much more opportunistic and random than that targeted. It’s a really interesting point that you make, but a lot so that the most common scams, as it turns out, I mean, we find out later, six and 10 are these calls. But what where where we are in the United States and this is what I’m trying to combat. I mean, something said six and 10. What do you mean? Six in 10 of the frauds that get reported, these kinds of that that involve cyber and when I say involved cyber, I mean, maybe they get a text message, maybe they get an email, maybe it’s a pop up on their phone telling them that they have malware. Maybe it’s a website. Often it’s a phone call.
[00:08:06] But when we put all these different had the lifetime that the extended warranty on my car thing does not fall under cybercrime.
[00:08:14] It well, I’ll get there, yeah, because it kind of does, but I sometimes like playing along with them before telling them.
[00:08:22] But but I don’t understand because I don’t have a car. You don’t have a car at all.
[00:08:28] Yes. And this is the real problem. There’s no definition in American law enforcement of what cybercrime is. And even worse, there’s no understanding of what the word cyber means. Everybody uses this word cyber, and it’s this huge slush fund of all these different things. And I was referring to it as a Rorschach test, because I say to you, like, we’re having a conversation, I say, well, I’m in the cyber thing. And you’re like, oh, yes, cyber. I could be talking about network intrusion. And you could think of think I’m talking about Sims or. Yeah. Phone calls. Right. I would not consider cyber. Yeah. So so what we had to do was make a definition and the Europeans or a few years ahead of us in this and they have already broken this out into what they call cyber native crime. Now that’s that’s like, you know, the fat guy in the basement hacking into computers that President Trump was talking about. Right. It’s it’s crimes that couldn’t exist without the Internet. It’s I hack into your computer and I go in or I go into your Bitcoin wallet and I transfer money out of your Bitcoin wallet into my Bitcoin wallet, cyber natives. Right. That and we can refer to it as that. But it’s like, you know, for everyone remembers that movie WarGames from thirty five years ago. Yeah. Well, anybody who alive and then there’s other crimes which are just crime. They’re just basic crimes. But they they have some kind of a of a component that involves usually it’s communication tools like a phone or email or SMS. Sometimes it’s messing around with your cell phone.
[00:10:07] And so I’ll talk a little bit about SIM Swap, which is a pretty it’s a pretty devastating crime. It’s on the way down. But the those who get hit are it’s more devastating than ever. But I’ll describe it in a second. But these are what we call cyber enabled crimes. So it’s a it’s a traditional crime, like a fraud, extortion, grand larceny. But we were getting wrapped around the axle as law enforcement because it had this component that made all the detectives run into brick walls because it’s like, well, wait, wait a minute. They did what they got you on a cell phone and they told you to text something and then you had to go put Bitcoin in an ATM.
[00:10:46] You better call somebody else because, you know, this is already sounding too hard for me. And I don’t think it is that hard. It’s just that we’ve never trained any. But we never talked about it. We’ve never trained anybody to how to do it. And so that’s hard if you don’t know what if you don’t have a protocol and we don’t and I don’t mean the NYPD. I mean like anyway, then you can’t follow, it seems. What is the one? So, like, you’re sitting home on a Friday night and maybe your phone stops working and you look at it, you’re like, oh, that’s weird. Maybe you don’t even notice. Right. But you look down at your phone and it just it’s it’s got no service. So maybe you just think, oh, we are. So you restart your phone and then it still doesn’t work. So maybe you go outside to see if you can get better coverage and it still doesn’t work. And after a while, it dawns on you that your cell phone is not connected to the cellular network anymore.
[00:11:32] And what has happened is some criminal has called AT&T or Verizon or T-Mobile, and they’ve said, hey, I’m Bob.
[00:11:40] And I got you know, they’re impersonating you. They know your phone number. So they already got a little bit of research. They got your phone number and now they’ve got your email.
[00:11:46] Because, you know, I’m just taking a guess that Peter Moscow’s a Gmail dot com would be an address that you might have. I don’t know.
[00:11:53] I don’t ironic. A lot of people I could, but I couldn’t figure it out. Right. Yeah. And and anyway, you can email me, you can find my my e-mail. We can find it’s pretty easy.
[00:12:02] So if I know your phone number now, you’re, you know, I can call up a cell phone company. I could by the way, if I know your phone number, I can type it into a computer and for free I can find out who your carrier is. So now I call your carrier and I’m like, hey, this is Peter. I just got this new iPhone twelve. And it’s really great, except oh no, my old SIM card from my old phone, which was a rotary. It doesn’t fit in the new one. So I need to how can I do this? I got a new SIM card at Walgreen’s, but now they tell me that it doesn’t doesn’t work.
[00:12:29] Three times out of four, the customer service representatives say, OK, what’s the password on your account? And then they just hang up and call back till they get another one time out of four. They’ll be like, OK, what’s the new SIM card number?
[00:12:40] And you tell them a new SIM card number. Now they associate the bad guy SIM card with your phone and all of a sudden your phone stops working because they’ve got your phone number. As that happens, they go to your email, they say, I forgot my password. And your email sends a text message. Where to your cell phone, which is now their cell phone. Now they’ve got a text message. They log into your email with that, reset your password. Now you’re locked out of your own email. Now they’ve got your mobile phone and your email. So the first thing they do is they start looking through your email for anything that says Chase Bank, HSBC, Fidelity, Vanguard, and they find all your accounts. Now, how do those accounts get reset? Well, through a text message and an email.
[00:13:21] So are you saying that to stop verification, which for other reasons we don’t have to get into? I don’t yeah.
[00:13:28] Use two step verification is actually a security for its well to step verification using your cell phone. And that’s how it is a big flaw. Yeah. So what you want to do is something called Time-Based one time password, which is like Google Authenticator or OFFIE or duo, something like that, where it’s a it’s a program actually running on your smartphone that gives you that one time password every every 30 seconds, every 60 seconds that can’t be gamed like this. But a lot of people still use that SMS. We have seen people get their entire life savings drained in a matter of minutes. And I’ve also seen that the victims, when they lose their email, it can take months to get it back because you have to prove that you’re you, but you have no way of doing it because you don’t have your phone, you don’t have your passport. They’ve changed all those things. You’re locked out and you’re in a world of hurt. So that’s a that would be, you know, a that would be a cyber enabled crime because what they’re doing is human social engineering to try to trick people into changing it or they’re going into a store with fake ID saying that they’re used. So there’s a human or the store is in on it or the store is in on it, then actually it’s part of our pilot. We actually arrested some Confederate’s who were working in cell phone stores who were actually doing that. But the bad guys would come in. They paid them off. So. So you came in like the union army? Well, no, you know, detectives to go in and get just the Confederate part, sorry. So robust. We set up the we set up this thing. And the purpose of this pilot was to figure out how big the problem was. And we weren’t we weren’t trying to, like, make any arrests or he was just how big is the problem? How much money is lost just so that we can start the conversation. And the pilot went on for several months, eleven months study and four months of actual work in Queen. S, and we found that the actual number was about three hundred and twenty million dollars a year in New York City alone, just the five boroughs of New York City. Three hundred and twenty million dollars. About twenty thousand of these crimes happening in New York City is there? Did you estimate what the average rate is worth? Fourteen thousand dollars.
[00:15:41] So fourteen thousand fourteen grand? Well, you know, there’s no expense to failure.
[00:15:46] There’s a time expense and the labor expense. Yeah, but it doesn’t matter how many times you fail if you eventually succeed. Yes.
[00:15:53] One of the the the intel guys that the district attorney of New York, he said the guys who were doing crack in the 80s, selling crack in the 80s and selling untaxed cigarets in the 90s, they’re doing this now and the gangs are doing this now. So some of the surprising things that we learned, which I just want to interject.
[00:16:10] Oh, yeah. Is one contributing factor probably to the violence decline in New York as well.
[00:16:16] Yeah, a lot of those same guys and we did Martin Consti from NPR did a story about this. He came around with us for a couple of days and did a story about this. And his favorite quote at least was I said, you know, people think that this is people in Nigeria. This is knuckleheads in the Bronx. This is not like one of the prosecutors in Queens said, don’t tell me they’re in Jamaica. They’re in Jamaica, Queens, like they’re these are locals. And as it turns out, actually, the majority of these these actors are local or regional or at least national. And if they’re not, there’s there are a number of scams where they are controlled by overseas. And we’ve all probably heard the the overseas tech support calls. And those guys, the actors are overseas, but their money’s in America, their money is in the region. And because they need this just like anything else, it’s a business. And they have to have mules and mule herders. They have to have coordinators, they have to do money laundering and get the money collected and then send it out so you can put your hands on something. And this was a big shock. This was something that that really surprised us. Another thing that surprised us was the demographics of this. So we all think that this is an elderly problem. The median age was forty two of the victims who reported and there were I mean, an awful lot. Of digital natives getting caught up in this, one of the things when when Martin was doing the radio program, the first victim of the day was a 22 year old in Brooklyn in the projects, and he had sold his phone on eBay. And the guy who bought his phone looked in the phone and found videos, you know, sexy videos of him with his girlfriend and extorted him. And after the girlfriend broke up with him, he called the police and, you know, we we basically said, look, you know, we can work on it.
[00:17:58] And because it had been I think he waited a week or something like that, that the sooner you get in touch with the police, the more chance they have to track it down. But it was there were a lot of young people who were getting hit by these things.
[00:18:09] And that presumably is that just whichever detective picks up the phone in the precinct or is that a specialized detective to deal with these tech issues?
[00:18:19] So that’s that’s a really great question. And that was that was part of it came up well, because it was one of the questions that we didn’t anticipate having to think about. And as it turns out, what law enforcement does, because it’s cyber and cops have 10 thumbs and they don’t like cyber, who do we have? Who knows about cyber? And it’s always the iChat guy. It’s always the guy doing child pornography. And there’s one of them. So there’s like one guy in the police department who knows forensics. So now suddenly the forensics guy who’s often a civilian. But, you know, NYPD, there’s a lot of sworn guys who do forensics, but they’re not frontline investigators supposed to be doing everything. But everything gets thrown on their desk and they don’t have they just don’t have the time. And it’s also not appropriate most of the time like that. He may think any detective who knew could be like, OK, well, you know, who bought it on eBay, let’s get a warrant and serve it to eBay and find out who bought the phone and where it was said. Now we’ve got a name and an address. And it’s pretty damn simple, right? You don’t have to do a lot of rocket science, pocket protector, super secret squirrel stuff. It’s just basic police work. When we solved SIM SIM swaps when the NYPD.
[00:19:29] I don’t know. Maybe people don’t know that, but it’s pretty routine for police departments to get to you get warrants and serve them to the to the phone company or whatever. But that’s a pretty common routine practice. I’m sure they have someone on there and who just deals with that.
[00:19:44] I’ll tell you that one of the one of the SIM swaps that we did was and it was this guy, he was on the grand larceny, the grand larceny squad in the DA’s office. And he’s a really good cyber guy. But when we talk to the victim, he called up AT&T, got a customer service representative, got the got the victim to say, yes, you can talk to this guy. And he’s like, hey, there was a SIM card put into that phone. Can you tell me the number of that SIM card and the AT&T guys like. Sure. Given the number. He said, OK, were there any other phone numbers that our phone accounts that had that same SIM card attached to it in the last year? The guy’s like, oh, oh yeah, there’s a whole bunch of them. Can you please tell me all of those accounts we had a list of of victims right there? As a matter of fact, it took that detective longer to get the clearance to go to Columbus, Ohio, and lock this guy up than it did to figure out who he was and when this was great. And talk about, like, not having to have special skills. They got Columbus, SWAT, and they went to this guy’s house to serve the search warrant and get all of his devices because they knew who he was. They kicked open the door. There he is. He’s on his phone holding it up on his computer when they walk in the door. So John is like, you know, he’s like, OK, so what’s the password to your phone? Was like, well, I’m not telling you that. So John’s like, OK, looks at the girlfriend. He goes, what’s the password to his phone? She’s like nine, eight, seven, three one type. All of the evidence is on his phone. Now, that guy ended up getting arrested and getting charged and convicted. And none of that had to do with having a computer science degree. It’s just basic police work.
[00:21:15] Let ask not good. Probably I’m not. Good question. How do the cops call the victims and convince them they’re cops if they’ve already been victimized in this manner before?
[00:21:23] Yeah, so good question. So the initial victim usually reports there’s a lot of reasons. By the way, we found out a lot of reasons why people don’t report, starting with I’m too stupid to live like, oh my God, I’m just so embarrassed. I can’t believe I fell for that. Once they figure it out, there’s some what the fuck are the cops going to do? Like, why would I call the police? Because they’re not going to do anything. And that’s often not wrong. I maybe actually do have an arrest warrant out for me. Maybe I’m not really wanting to call, but there’s there’s a few of these reasons why they don’t call. But but if they call and if they report and they don’t get laughed at, you know, and they managed to get a report done, then it’s really a question of and my the guy I was working with, he was a he was an officer that I got. So, you know, I was a civilian and NYPD, he was an officer. We would go together to the victims that we identified. Then we would walk in and, you know, so now it’s a guy in uniform, another guy, and we’re talking to them. We have all their information.
[00:22:23] So it’s pretty easy to to convince them at that point. OK, but and that’s not a bad question. Like, all this stuff is brand new, right? We haven’t done it before. We made an app that help other victims.
[00:22:35] If in New York City, are they generally in New York City? I mean, why would I assume they’d be scattered all over America?
[00:22:43] Well, we were the NYPD, so we were only going to victims who called in to the NYPD or showed up at all.
[00:22:50] OK, but I’m assuming when you got that list of dozens of other. Yes. Victims, how did you how did you deal with that?
[00:22:57] Three of them were in New York City. So that gave that gave the NYPD and the district attorney of New York the jurisdiction to they could investigate that. The rest of them were outside of New York City. And then I believe, Danny, the district attorney of New York, did referrals to all the other agencies and said, hey, we arrest. And now the money was gone by that point. It was ten days, half a million dollars that kid took. And he had just spent all the money so that, you know, wasn’t the restitution. But they did get some justice because the guy said we made an app for the patrol guys to be able to ask the right questions. And this was the biggest barrier that we had to to getting this approved.
[00:23:42] There were a lot of people in the NYPD not not at the chief level, but at the sort of lieutenant level who were like, no cops going to give a crap. You can’t get cops. They don’t care. They’re not going to do this. They’re too lazy. They’re you know, they said all these terrible things. We went around and Louie and I that the guy I told you about, we trained more than seven hundred APD officers. We would go to the roster. We would go to go to the roll call in the morning and the afternoon. The evening. I’ll tell you that these cops were frustrated by these and they were pissed off at these things.
[00:24:14] And they when we told them, you know, we were able to say, hey, in your precinct last year, one point four million dollars was taken from your the people who live here in your precinct. And they were pissed and they all heard about it before, but they never knew what to do. And as soon as they heard that there was something that they can do, they were on it and all of them wanted to do something. And when we gave them this app that I’m just about to tell you about, they all wanted to do something about that, too. And they used the app. So we had, you know, the every one of the people we gave the app to used it at least once to try it out. But then many of them not. I don’t even think it was most, but many of them used it on calls that they were on to actually do it. And we have all the user statistics which show that they were using the thing. So you give the cops a chance to do something. I don’t care what your politics are. People don’t become cops because they don’t care. They don’t become cops because of the money they want to help.
[00:25:03] And so if you give them the ability to help, they will help. We made an app that just gave them. They had to answer four questions what happened? What kind of crime was this? How much money was taken? How were they told to send the money and hit go? And then they get the questions to ask? They wrote those questions down. Those went to the detectives and that was how we did it. The reason that I’m talking to you now is a lot of other agencies heard that story on NPR about a year ago.
[00:25:32] And I’ll send me the link when you can and I’ll put it up on the air quality policing dot com website.
[00:25:40] I definitely will. And so a lot of agencies and also the National Sheriffs Association, they are saying we need to do something because just telling people to call the FBI and fill in a questionnaire is not getting us anywhere. We you know, we these are crimes and we have to do something. So when they do that, the first thing that I tell them is, oh, yeah, that app you heard about on the radio, I’ll give it to you free and it’s open source. You can it’s open source for law enforcement and for government. You can use it and you can customize it. I’ll show you how to customize it. And if you can’t customize it, I can introduce you to people in the open source community who will help you customize it, because it’s really easy.
[00:26:18] You don’t have to do any serious stuff. It’s you know, it doesn’t it doesn’t plug into your to your system. So it doesn’t have to meet federal standards of data security and all these other things because you’re not putting any information it you’re just getting information out of it. And I’m handing that out. So we’ve had agencies from Ireland and in several different places around the United States ask for help. And I’m perfectly happy to to make it available to government and help them figure out how to use it. And also to share the full report that I made for the NYPD before I left about exactly what we found in our study, because the study was really surprising to a lot of people.
[00:26:54] Yeah. How I can put it up on the website or how do you want if law enforcement is interested, how how should they take you up on this offer? Oh, that would be great.
[00:27:05] Yeah. If you can put it if you can put that up on the website and you can put like a link or use your mail link and have them, you know, just forward them on to me and I’ll be perfectly happy to, to talk them through.
[00:27:16] I mean, this is not like something I’m doing is going to be a direct way to contact you.
[00:27:24] Yeah. So this will be I think it’ll be episode forty one on quality policing dotcom.
[00:27:31] That’ll be awesome. Yeah, and it’s just just so people know this isn’t like a consulting gig, this isn’t something I’m doing for money. There’s, you know, there’s a few of us around who are just willing to to volunteer to help people get it, because I don’t care. I don’t care how you do it.
[00:27:46] If I give you the stuff, you figure out a better way to do that. Please tell other people. But this is something as a public service, I think we all need to do because it’s really hard. It’s really hard to get our brains wrapped around this. And I’ll tell you one last thing. Like cops, cops, patrol officers especially don’t like not knowing what to do. It’s their job to know what to do.
[00:28:08] You show up on scene and you’re the guy, right? Everybody’s looking at you to tell them how to behave and what to do. And cops, you know, they’re good at that. You know, you stand over there, you stand over there, you do this. And I got to fill out this form. You turn around. When they don’t know how to do that, they get really quiet and they just they just feel really uncomfortable because it’s just out of there. It’s out of their comfort zone. And I like to say that no cop in the history of cops ever got in trouble for doing nothing. And, you know, it’s a tactic I’m sure you’ve used yourself. If you’re not sure what to do, wait a couple of days, you know, but something will happen and usually they’ll just go away.
[00:28:48] This is a way to solve that problem because you give them even just a little bit of guidance and they’ll take it from there. The the strategy here is you get the patrol officers because they’re the first ones to get these calls right. The patrol officers have to understand this and not be afraid of it and not think that it’s something too complicated for them or for someone else. You know, it’s a crime victims. If somebody said that they got hit over the head with a pipe and they took their wallet, you’d be running to help them. If somebody takes fourteen thousand dollars from one of your residents and you’re like, oh, that’s not a good that’s not good policing. That’s not good police service. So take the notes, take good notes. You don’t have to be a scientist. Just write down what they’re saying. And and, you know, if they say that they had to put in Bitcoin, get their receipt, if they if they they use the Bitcoin ATM, get that receipt that’s got all the information that a detective needs. If they say that they got tech that they had to text a gift card to somebody, get the phone number they texted it to, what kind of gift card was it? An Apple Home Depot. Write it down, because now you can start figuring out what the bad guys are using and getting intelligence. If the patrol officers do that, they give it to the to the detectives. Now, it’s not a piece of shit from the moment it hits the detective’s desk and they have the ability to start some investigation, even if they’re not that great at it. They have a starting point. And, you know, you give a good detective a starting point and they’ll usually figure it out. So it’s it’s really all about basic police work and it’s about just working the case that’s in front of you. And, you know, there’s some other problems upstream, like the DA’s don’t want to take the cases because they’re elected and they don’t understand it either. That’s tomorrow’s problem. Let’s figure out how to get the cases in the system start to count it. Because I’m telling you, when we see these numbers from the FBI about cyber crime, those are very, very underreported. FBI says it themselves. Those are very underreported. This is a huge problem in this country. And the only way to fix it is to actually fix it.
[00:30:39] We should also mention, just for the hell of it, that case anyone is like, who is the civilian telling us what to do? That before you worked for the NYPD, you were sworn officer and a detective working in these. Yeah. So you have that experience, actually.
[00:30:55] Yeah. And I’m and this is the thing like down down in Texas where I was working, we would get a lot of cases. Sometimes it was ransomware in those, you know. Yeah. That does go to the FBI. They have got really good people at the FBI. They have really, really good investigators for like cyber native crime. That’s true. But oftentimes we we can get these kinds of scams and we would go and just do exactly what I’m saying, which is, you know, I didn’t just like make this up when I got to NYPD, we had a lot of experience. And my agency, I think we were one of the first and we’re like one hundred, one hundred man agency.
[00:31:23] But we were one of the first people to give identity theft recovery tips to people. We had a whole list of things that you could do if you were a victim of identity theft, if you were a victim of cyber crime, like how you could figure out what happened and try to get some help. And that was actually one of the first things that that got me talking to NYPD was that that we were doing this in this tiny little town in Texas. I mean, I’m from originally from New York. So it was kind of a nice fit, but that was how it started.
[00:31:48] All right, thanks. This has been really informative.
[00:31:54] Well, thank you very much. And get Two-Factor authentication on your you know, it’s really important.
[00:32:00] I just know it wasn’t that it was that the whole texting, I was like, what if I lose my phone? Yeah. I never I never have trusted my phone. I don’t trust my phone for anything.
[00:32:08] But I’ve certainly never trusted as a security device people get robbed of phones. I’ve always. Yes, true. You know.
[00:32:18] Well, that’s and you know, I did an article a couple of years ago for USA Today about how your phone was actually never intended to be a security device. And SMS is an inherently insecure protocol. It’s just not done. We’re using it. You know, it’s kind of like the Social Security number. That’s when I was 15. ID number. Yeah. You know, I remember we’re old enough that we remember our Social Security card actually used to say right on it, not for identity if I had for identification purposes. And now suddenly we’re using that and look how well that’s worked. And SMS authentication, it’s a really flawed system.
[00:32:55] And, you know, I if I if I’m working with an online bank or something like that, I’d take my money someplace else. I just don’t do it if they want to for real authentication, because it’s just too easy to break in and take your money.
[00:33:07] Hmm. Well, on that note, that’s why I keep mine in my mattress.
[00:33:12] Oh, wait.
[00:33:15] But don’t worry, I put a box on anything else or if I got all I mean, it just came on the blather, that stuff, and.
[00:33:24] Yeah, that’s great. Nick, you can come back anytime. You’ve earned that by starting this podcast with me. So I’m with Nick Selby will be why there’ll be some information on quality policing dotcom related to this information. And I am Peter Moskos and it’s good to have you back, Nick. And thanks for listening, everybody. Thanks a lot.